Introduction
HTTPS inspection, is one of the greatest new features in TMG 2010. Prior to TMG, ISA Server was able to perform Inbound HTTPS inspection ( SSL bridging ), however, since the first generation of ISA Server, Outbound HTTPS Inspection was not available. Finally this feature is introduced with TMG 2010. In this article, I will be showing you how to enable and configure HTTPS Inspection.
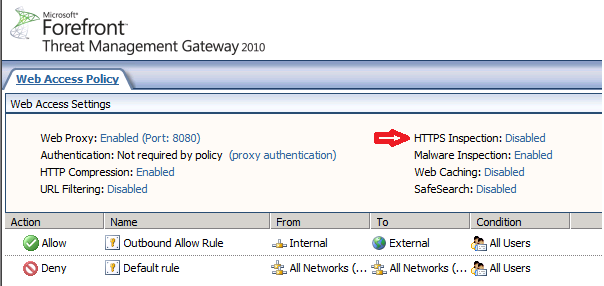
By default, HTTPS Inspection is disabled. To enable it, follow the below steps:
- From the Left side node, click on Web Access Policy

- Then from the right side node, and under the Tasks tab, click on Configure HTTPS Inspection

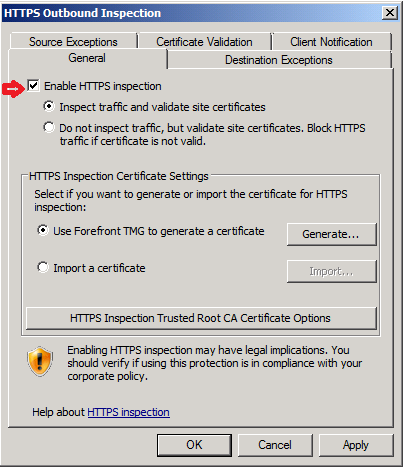
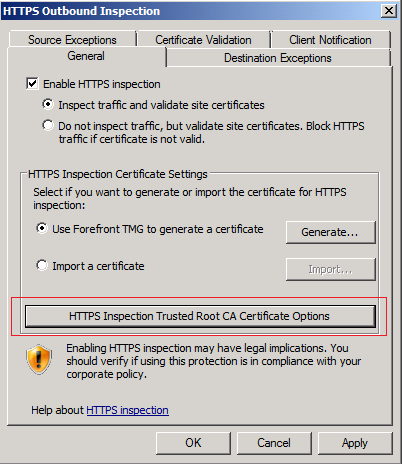
- The HTTPS Outbound Inspection window will open, under the General Tab, enable the checkbox Enable HTTPS Inspection

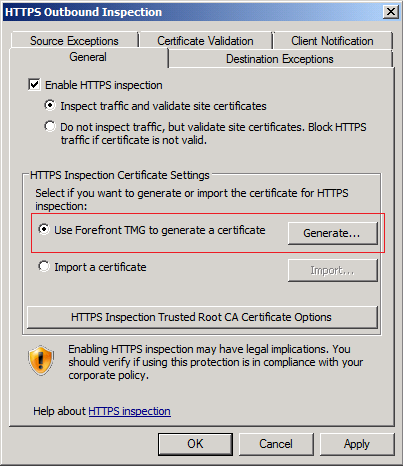
- Select the Use Forefront TMG to generate a certificate and then click on the Generate button to generate a certificate for TMG, which will be as a handshake between the server and its clients to decrypt the encrypted channel and inspect it.

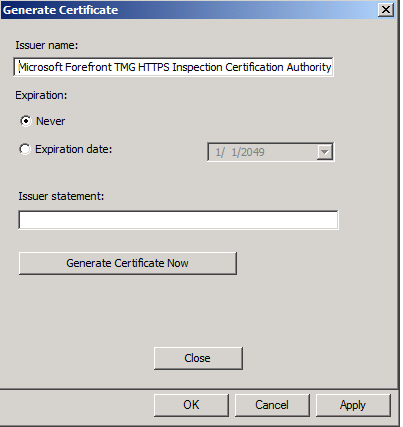
- In the Generate Certificate page, you can change the issue name to whatever you want, for example TMG Server, as for the expiration, its up to you if you want the certificate to be expired on a specific date, or to Never. Keep the issuer statement textbox empty. Then click the Generate Certificate Now

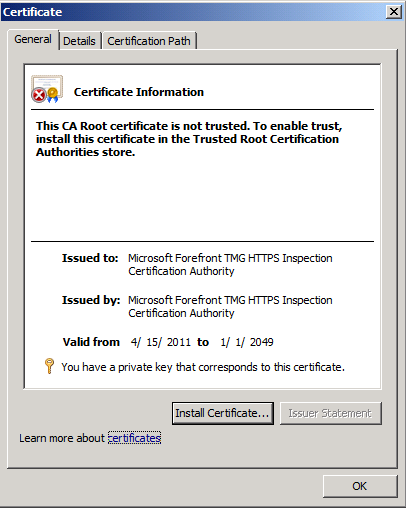
- The generated certificate will be opened, and is currently installed on the TMG Server, don’t click on Install Certificate… , Click OK

- To configure the deployment options for the generated certificate, click on the HTTPS Inspection Trusted Root CA Certificate Options .
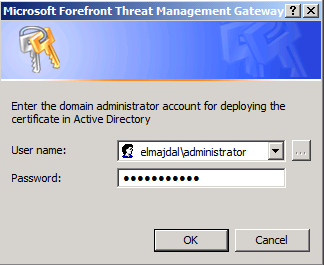
 As you can see, there are two options to deploy the generated certificate, either Automatically through Active Directory (Recommended) or Manually on each client computer. If you have an active directory, then keep the default option selected. This will make the certificate be installed by active directory saving administrators the overhead of manual deployment. The certificate has to be installed with a domain administrator privilege. Click on the Domain Administrator Credentials, type the username then click OK
As you can see, there are two options to deploy the generated certificate, either Automatically through Active Directory (Recommended) or Manually on each client computer. If you have an active directory, then keep the default option selected. This will make the certificate be installed by active directory saving administrators the overhead of manual deployment. The certificate has to be installed with a domain administrator privilege. Click on the Domain Administrator Credentials, type the username then click OK


 Else, if you don’t have Active Directory, then select the Manually on each client computer, export the certificate, and then go physically to computer by computer and install the exported certificate.
Else, if you don’t have Active Directory, then select the Manually on each client computer, export the certificate, and then go physically to computer by computer and install the exported certificate.
To see the generated certificate, click on the View Certificate Details… button and you will see the certificate that was just created moments ago. - Once you set your options, click OK to go back to the HTTPS Outbound Inspection window.We have now enabled HTTPS Inspection, created a certificate and have selected the method for the certificate deployment. What remains is, fine tuning it to meet your requirement.
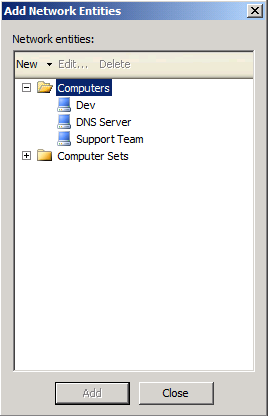
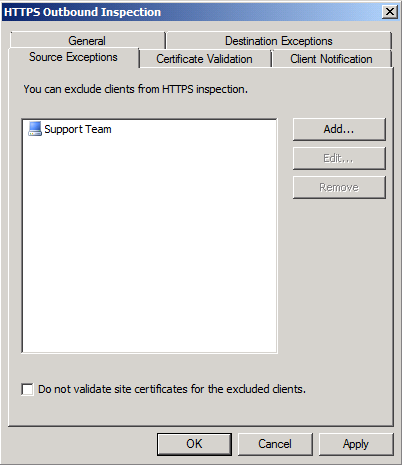
- Click on Source Exceptions Tab. Under this tab, you can exclude clients from HTTPS inspection, for example, your boss don’t wish his https connections to be inspected. So you will need to add his computer IP. Click on the Add… button to add whoever you want to exclude from HTTPS inspection.



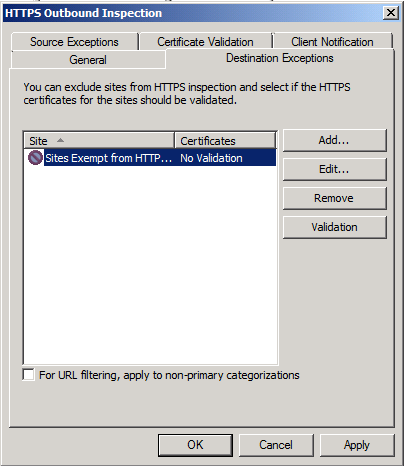
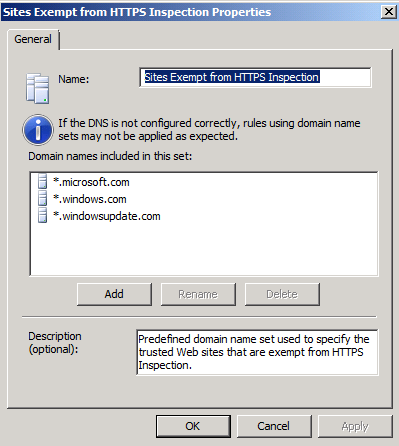
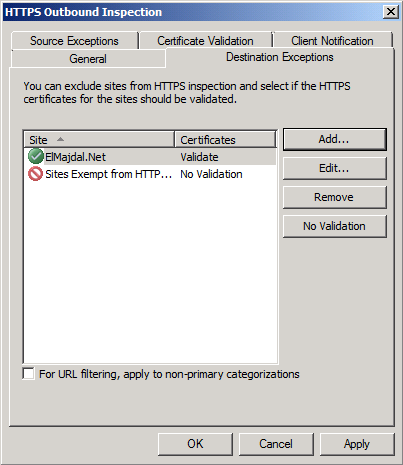
- When done with the Source exceptions, click on the Destination Exceptions, where in this tab, you can exempt destination from being inspected, and by clicking on the Validation button, you can select whether the https certificate for these exempted sites should be validated or not. By default, some Microsoft websites are exempted from being inspected, you can add any of Microsoft website to this Domain Name Set.
Also you can add your own website to be excluded from being inspected.



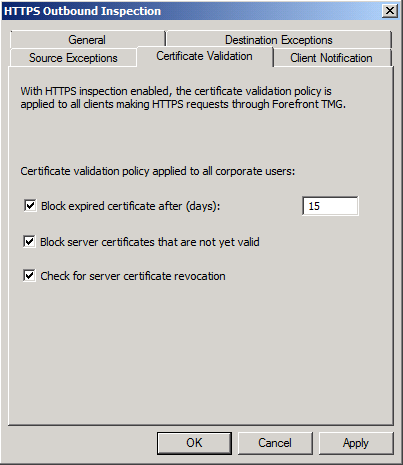
- Under the Certificate Validation Tab, you can set the options for what to do when a certificate is expired, for server certificates that are not yet valid and for server certificate revocation. make any changes, if required.

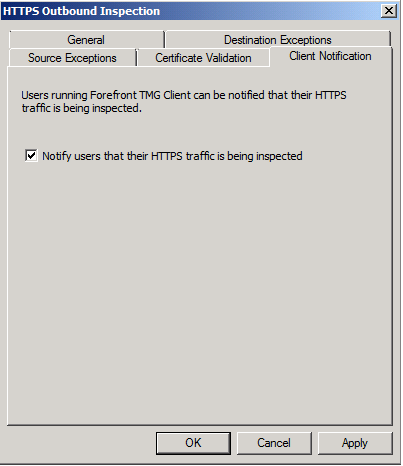
- As for the Client Notification Tab, its better to enable the option Notify users that their HTTPs traffic is being inspected. Check with your corporate policy, as HTTPS Inspection might have legal implications, and so users should be notified that their traffic is being inspected.

- Once all of this is done, click on the OK button, the HTTPS Outbound Inspection windows will close, make sure that you click the Apply button, so that changes take effect.
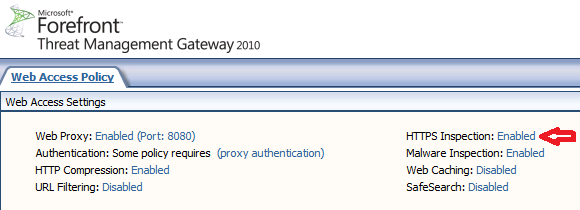
 as you can see, now HTTPS Inspection is enabled.
as you can see, now HTTPS Inspection is enabled.

Summary
HTTPS Inspection is one of the greatest new feature in TMG 2010. If you have a active directory domain, then the deployment of the HTTPS Inspection Certificate can be deployed automatically via Active Directory. The options available with HTTPS Inspection, gives the administrator the freedom to exclude either sources or Destinations from HTTPS Inspection.


 As you can see, there are two options to deploy the generated certificate, either Automatically through Active Directory (Recommended) or Manually on each client computer. If you have an active directory, then keep the default option selected. This will make the certificate be installed by active directory saving administrators the overhead of manual deployment. The certificate has to be installed with a domain administrator privilege. Click on the Domain Administrator Credentials, type the username then click OK
As you can see, there are two options to deploy the generated certificate, either Automatically through Active Directory (Recommended) or Manually on each client computer. If you have an active directory, then keep the default option selected. This will make the certificate be installed by active directory saving administrators the overhead of manual deployment. The certificate has to be installed with a domain administrator privilege. Click on the Domain Administrator Credentials, type the username then click OK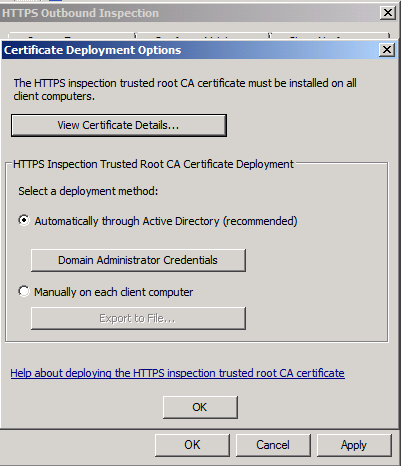
 Else, if you don’t have Active Directory, then select the Manually on each client computer, export the certificate, and then go physically to computer by computer and install the exported certificate.
Else, if you don’t have Active Directory, then select the Manually on each client computer, export the certificate, and then go physically to computer by computer and install the exported certificate.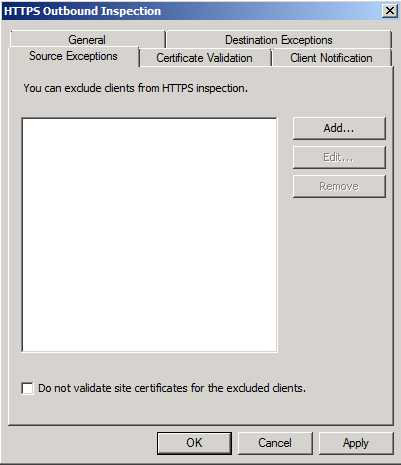
 as you can see, now HTTPS Inspection is enabled.
as you can see, now HTTPS Inspection is enabled.